In the digital realm, ensuring information security is paramount to protect users against various threats like phishing or other malicious attacks. One of the most effective ways to enhance security is by using authentication tools like the Sender Policy Framework (SPF). This tool ensures the reliability of email senders. This article, intended for the general public, offers a concise and well-structured overview of SPF and its functions.
SPF Origins: An Authentication Protocol
Since the 2000s, as the use of the Internet was gradually becoming mainstream, email stakeholders realized the necessity to develop tools that clearly identify email senders, in order to combat spam and phishing. Thus, the SPF was born as an authentication protocol.
Today, outlined in the RFC 7208, it links domain names to specific IP addresses, making identity spoofing much more challenging. In essence, SPF allows the email receiving servers to identify you as a legitimate sender, thus limiting the bulk sending of unwanted messages.
How SPF Works ?
- Associations: SPF allows one or multiple senders, identified by authorized IP addresses, to send emails from a specific domain.
- Limitations: If an IP address isn’t listed in a domain’s SPF records, it will be deemed illegitimate by the destination server. This trait makes SPF a deterrent against phishing and significantly limits the use of free webmail addresses for bulk sending.
- Legitimacy: Adopting the SPF protocol showcases to the email community your intent of being a genuine sender and employing suitable practices.
Integrating SPF Elements
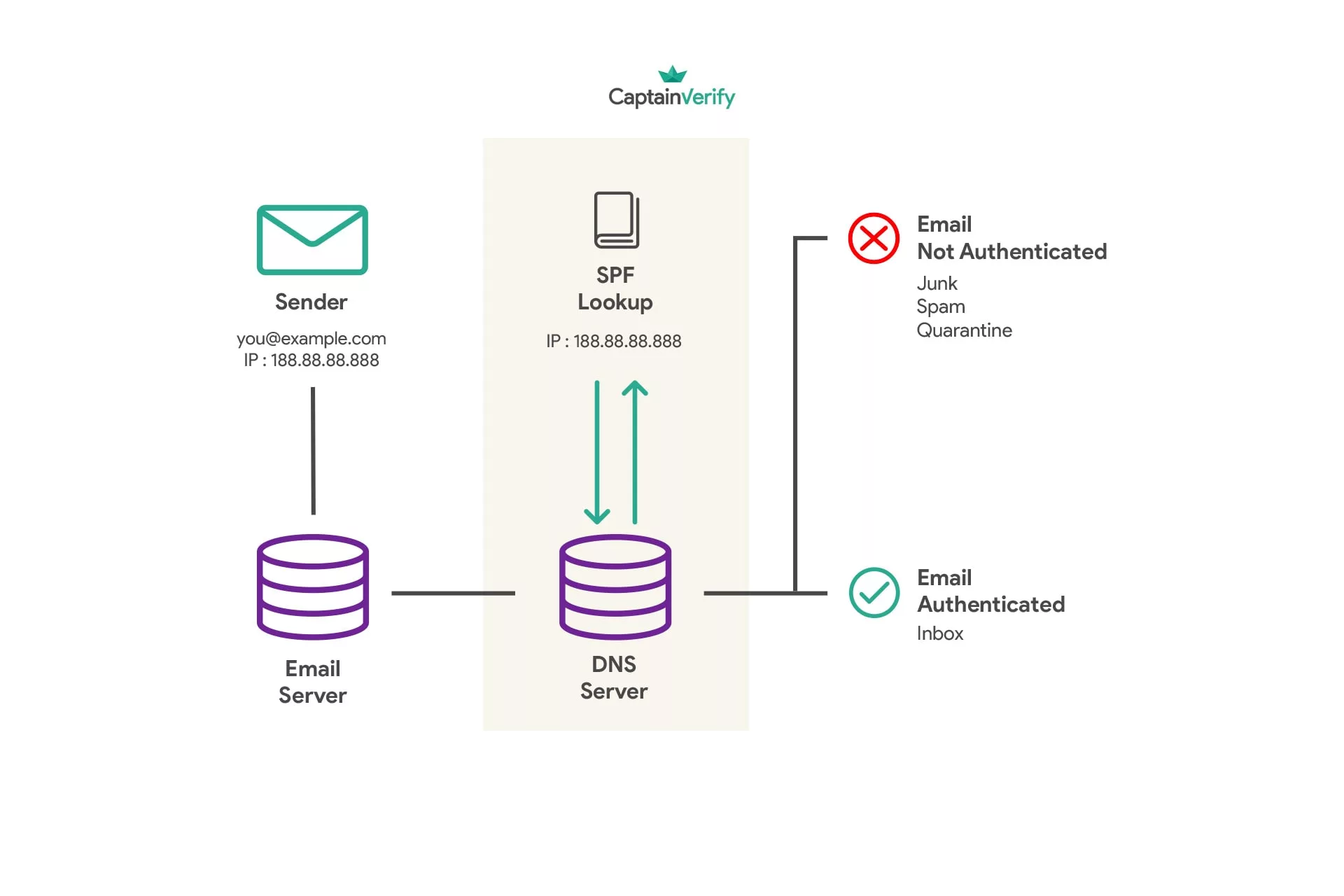
The SPF authentication standard is based on the exchange of information between the sending server (the one you use) and the receiving servers. It takes the shape of a TXT record containing the IP addresses allowed to send emails for the domain; usually, this refers to your brand’s website URL.
v=spf1 include:yourdomain.com ~all
If the sending server’s IP address matches one of the addresses listed in the SPF record, the receiving server will consider the email legitimate. If not, the IP address will be deemed illegitimate, potentially leading to the message being rejected or categorized as spam.
It’s vital to emphasize that using webmail addresses such as Gmail, Microsoft Outlook, or Yahoo Mail for large audience mailings is strongly discouraged. These providers not only limit such mailings but also, you can’t prove that you genuinely own these domain names.
SPF Limitations
There are certain limitations with SPF, which can be circumvented by combining SPF records with those of DKIM and DMARC. Some of these limitations involve cases where spammers spoof only the address mentioned in the “From:” field of the header rather than fully spoofing the sender’s domain name. It’s also worth noting that SPF will not be effective if your email is forwarded to another person.
Pairing SPF with DKIM and DMARC Protocols
To address the aforementioned challenges and bolster the protection of your sender identity, it’s highly recommended to couple SPF with the DKIM (DomainKeys Identified Mail) and DMARC (Domain-based Message Authentication, Reporting & Conformance) protocols. Doing so will significantly heighten email exchange security and affirm your legitimacy to recipients.
In conclusion, implementing the Sender Policy Framework (SPF) is a vital step for anyone aiming to maintain their reputation as a trustworthy and secure email sender. However, it’s crucial to remember that SPF is but one component in ensuring optimal email security. Pairing this protocol with DKIM and DMARC is undeniably a crucial complementary step.







