Before landing in the inbox, an email goes through several treatments that will make it possible to define if it is legitimate or not. Among these steps and processes, we…
Although we are numerous and numerous to exchange dozens of e-mails every day, or more, some points are still fuzzy. When you send an email, the field “To” allows you…
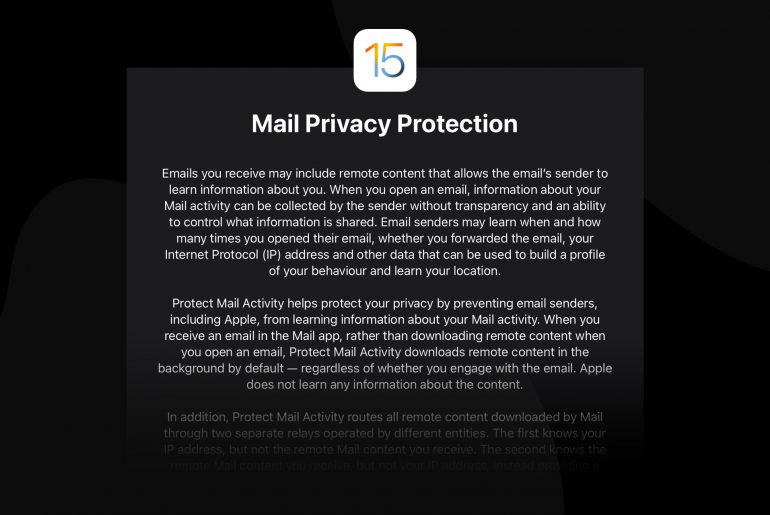
With the arrival of the iOS 15 update in September 2021, Apple once again proved its desire to prioritize the confidentiality of the data of its users. The brand has…
A CNAME (Canonical Name) record is a type of DNS entry that points a domain name to another domain instead of an IP address. For email marketing professionals, mastering CNAME…
One of the essential factors to ensure the success of your email sending operations is choosing the right port for your emails. In this article, we will explore the main…
And if you were told that there was a legal, inexpensive and more or less easy way to get key information on a subject? This is what OSINT allows, a…
The main purpose of any respecting web marketing campaign is to reach the recipient inbox. A journey shot, and especially monitored by organizations responsible for evaluating your reputation as sender.…
Once is not customary, we speak to you here about email deliverability! A little-known but powerful tool to optimize this deliverability is Microsoft Smart Network Data Services (SNDS). If you…
It is possible to write an email address with the wrong syntax, and it will be invalid. Indeed, there is a clear and precise way to structure an email address…
With the growing number of spam and unwanted mails of all kinds, more and more visitors are saving their personal email address using single-use email, a bit likewise a digital…
Catch-All emails have advantages and disadvantages. They risk creating rebounds and negatively impact your delivery rate, but can also open the door on significant contacts. That’s why it’s important to…
A true bridge between what the client expects and what the company delivers, the POC orchestrates exchanges, maintains consistency in communication, and saves everyone valuable time. Let’s discover together who…
Your team is looking for new accounts, but your files are not progressing. Buying ready-made databases? Too risky. Collecting addresses one by one? Too slow. In between, there is a…
Gmail, an essential tool for accessing inboxes, is preparing to significantly tighten its requirements for senders. Starting November 2025, Google will introduce modernized controls and increased transparency during rejections. For…
We cannot emphasize it enough: the quality of your mailing list is crucial. Invalid or outdated emails can not only reduce your deliverability rate but also harm your domain’s reputation.…
Today, we focus on two very useful tools that are often confused: the email finder and the email verifier. At first glance, “finding an address” and “verifying an address” seem…
Grand Cleaning Time has come for your contact lists! It’s time to dust, rub and shine this inventory of valuable names for your email marketing campaigns, and so for your…
Whether it’s to preserve the confidentiality of your communications, avoid persistent spam, or simply test a service without disclosing your main email address, disposable email platforms have become almost indispensable.…
With the explosion of Chat GPT and other platforms, Artificial Intelligence has taken on a significant role in the professional world. Marketing experts are not spared from this technological revolution.…
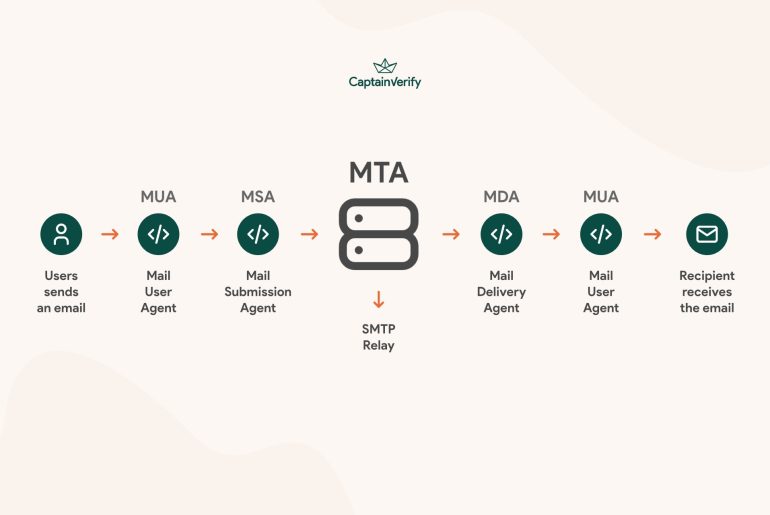
While marketers typically talk about segmentation, open rates, or personalized content, the MTA and verification work behind the scenes to ensure that your email campaigns reach the inbox. Today we…
The use of email marketing in the field of e-commerce can be extremely efficient and paying. Increased sales, customer engagement / prospects, increased loyalty, useful information sharing, etc. This versatile…
Customer’s life cycle and emailing are directly related. Indeed, optimizing the relationship you, business, maintain with your customers by accompanying them from beginning to end, and building with them a…
It is quite common to associate newsletter and emailing, in the sense that these two marketing communication tools may seem similar and, as a result, be confused. However, there is…
The world has never produced as many data, especially because of digitization. Smartphones, social networks, social media, online services, connected objects, etc. The mass of information that passes every day…
Sending emails is essential for businesses. However, sending an email to a person is one thing, getting it to its destination is another. What happens to the famous bounce messages…
Given the vast number of messaging services available today, one might wonder what a solution like Mail.com is truly worth. How credible is it really? What can be expected in…
Email was not born in an ivory tower. It emerged from drafts, trials, errors, and above all, curious enthusiasts seeking instant connection. Understanding this journey is to grasp how a…
Mastering the use of email aliases is no longer reserved for a circle of digital insiders. Today, this essential feature is becoming indispensable for effectively organizing one’s inbox, limiting the…
For some of you, the term “DNS” surely evokes something vague, or even ultra-technical, better left to the experts. Yet, this famous DNS is like the GPS of your emails.…
The authentication of an email allows the recipient to make sure the message is safe and that it comes from the right person. This is possible thanks to systems set…
Occasionally appearing in our inboxes or contact lists, the domain ymail.com often intrigues. Many question its validity or fear fraud, as this suffix is much less common than the traditional…
How to be sure that a message we receive is sent by a reliable sender? How to know if it is a legitimate email and not an attempt at spam…
Personalizing your email address using your site’s domain name is a key step in improving your email delivery, optimizing their open rate and strengthening your brand image. Here are the…
The fact of buying and selling something is already in itself and always a social activity, an exchange between several parties. Since the advent of social media, much of this…
Spam traps are used to monitor, identify and block spammers. A very convenient system for recipients, but can cause serious damage to companies using sending emails in their marketing strategy.…
Online phishing, which aims to steal the confidential information of an individual through emails or false web pages, is a real scourge. It is a common tactic that it is…
Who controls the inbox still controls a part of the customer relationship. As digital channels multiply, the email remains one of the most effective tools in marketing. But for a…
In the current digital context, the most used communication mode of communication is sending emails electronically. Whether private or professional messages, the SMTP offers a reliable distribution since it is…
Different from spam and far from being as harmful, the Graymail is not better. Your sending of emails may be entirely legitimate, if they are not read then the commitment…
Do you want to reopen dialogue with customers or visitors who left your site empty-handed? That’s exactly the purpose of email retargeting, an effective technique that allows brands to reconnect…
The topic of sending an anonymous email raises many questions and concerns. As electronic communication is now ubiquitous in both personal and professional communications, the issue of anonymity in emails…
The newsletter is an essential, durable and redoubtably effective tool in a marketing campaign. Loyalty, accurate targeting, hike traffic, excellent king, etc. It is a communication lever that offers valuable…
When we talk about performance in email marketing, we often mention the open rate, deliverability, or even the
Email has become an essential part of our daily lives and professional activities. There are two main methods for managing your emails: webmails and email software. Understanding the distinctions between…
Since email is one of the primary means of communication and is ubiquitous in the professional realm, robust protection is essential. Indeed, the proliferation of junk mail and phishing attacks…
Imagine receiving an alert as soon as a prospect clicks on a link in your email, or having your CRM automatically update when a contact unsubscribes. No need to go…
DomainKeys Identified Mail (DKIM) is a cryptography-based authentication mechanism for email sending. It allows for the verification of the integrity of messages as well as the legitimacy of the sender,…
In the digital realm, ensuring information security is paramount to protect users against various threats like phishing or other malicious attacks. One of the most effective ways to enhance security…
The proliferation of spam and irrelevant emails represents a daily challenge. Google, through its Gmail service, continues to innovate by employing the most advanced technologies to offer an unparalleled user…
The IP address is a key point in the field of emailing, and the reputation of this same address is essential to ensure the deliverability of your sending, as it…